The goal is to build a public network (guest WLAN, hotspot, call it as you like it) with restricted access:
- Only several services are allowed (e.g. surfing).
- Clients from network 1 (192.168.4.0/24) shall not be able to communicate with hosts of network 2 (192.168.2.0/24) and vise versa.
Most of the tutorials for OpenWRT only cover this scenario where your OpenWRT device is the only router in the network.
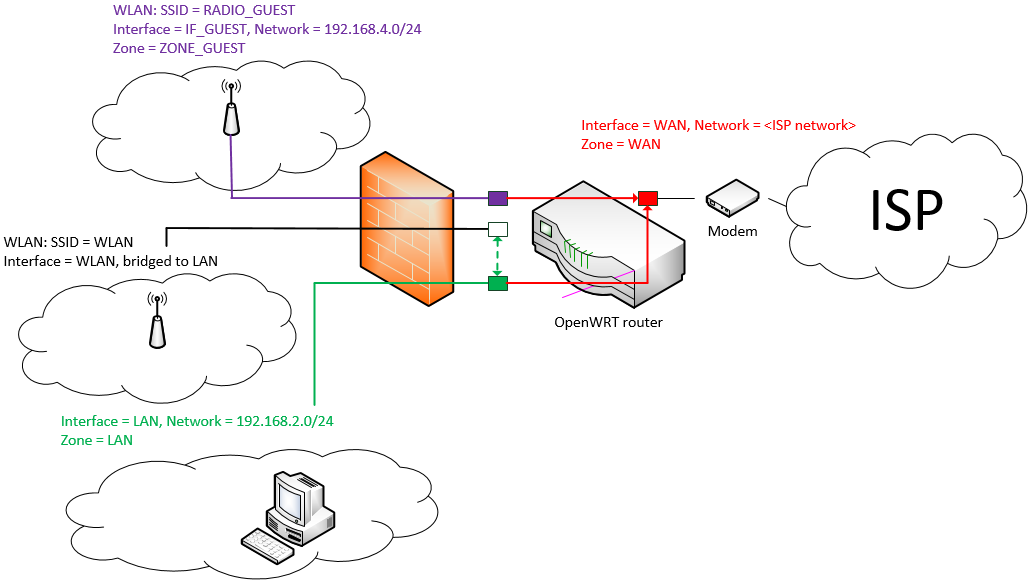
with a policy that allows forwarding traffic from the zone ZONE_GUEST to the internet (zone WAN) via the interface WAN.

Adding a few rules to the firewall is all you have to do then. It is a very practical way to easily allow your guests to use your internet connection without allowing them to communicate with clients in the zone LAN. If you wish to set this up, visit the OpenWRT page.
How about this scenario?
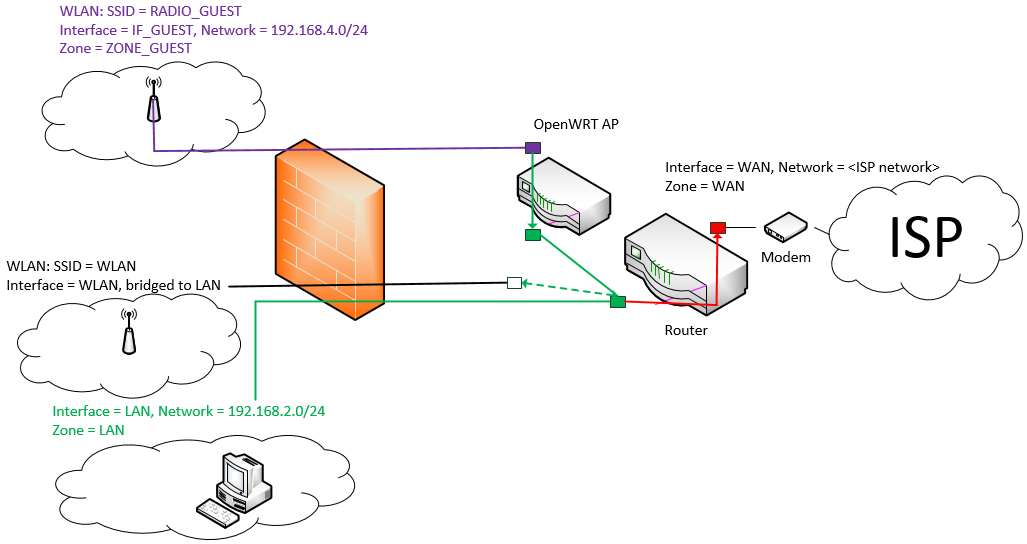
If you have an existing network and only want the OpenWRT device to be a dumb Access Point (AP) that uses your LAN resources you won’t find as many tutorials. Traffic originating from zone ZONE_GUEST has to be forwarded to the zone LAN instead of WAN. What you need to do is:
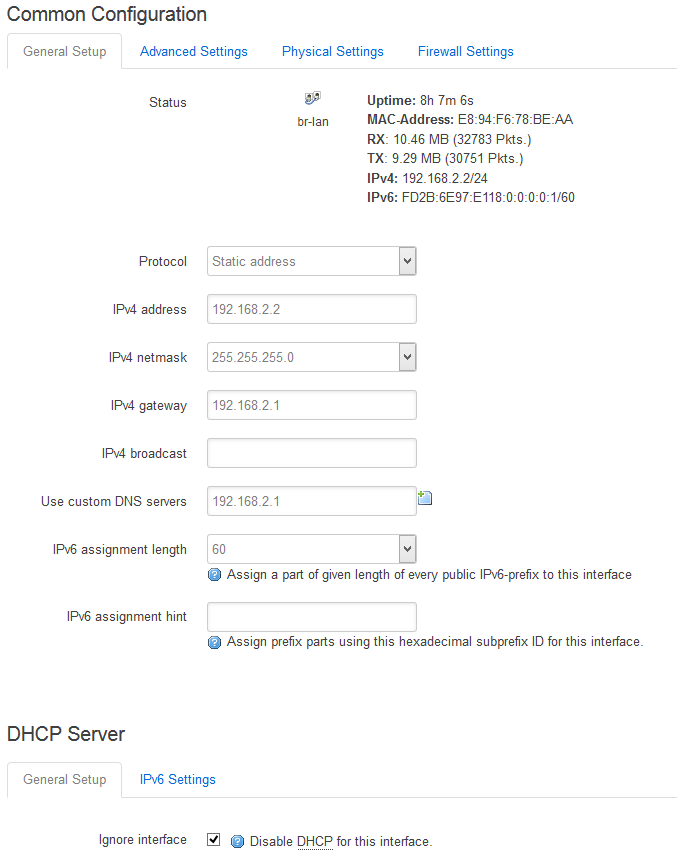
Edit your LAN interface:
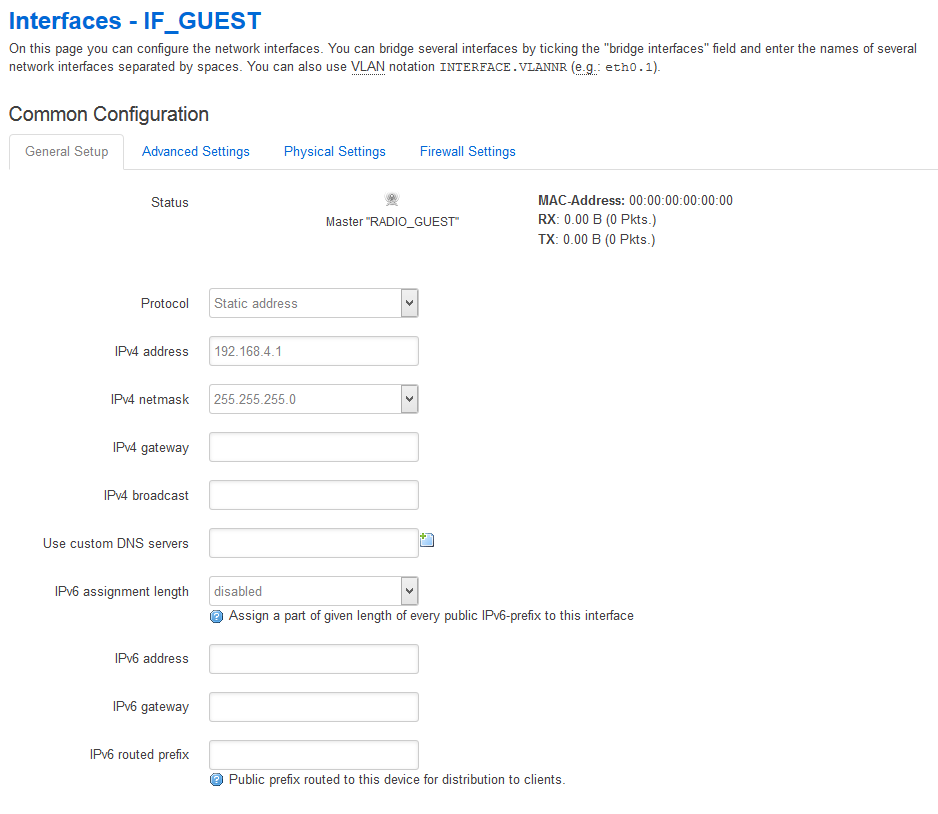
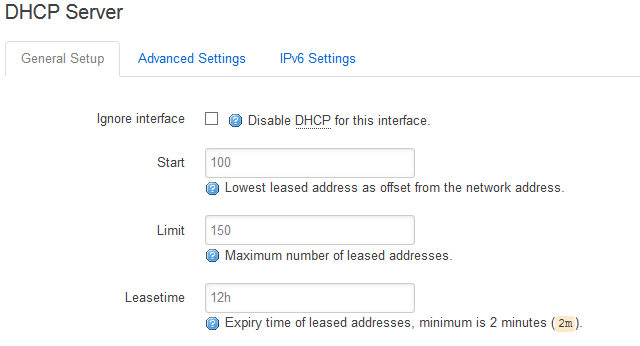
Adapt it to your existing network configuration (DNS, gateway, …). Don’t forget to turn off your DHCP for this interface. I assume that there is already a DHCP server in your network. If not you may have good reasons for that and should turn it off in your AP as well.
Create a new wirless network:
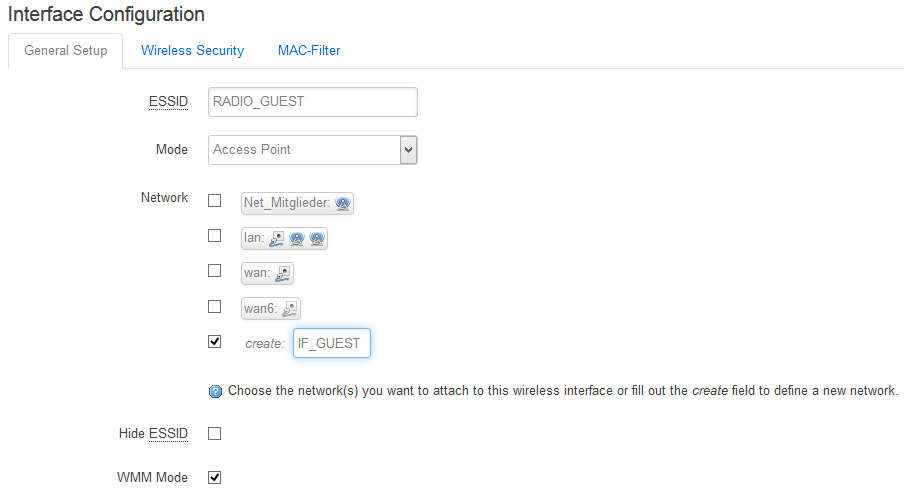
Edit the new interface:
Under “Common Setup” choose:
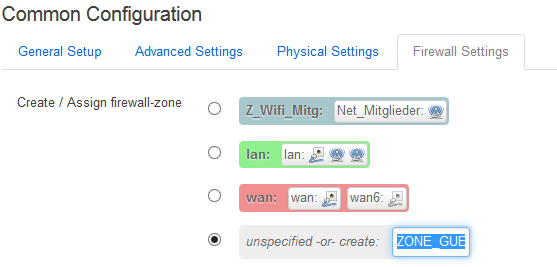
Under “Firewall Settings” choose:
Edit the firewall settings:
General settings
What is not shown here was not touched. So I focus only on the differences to the standard configuration.
This may be your general settings:
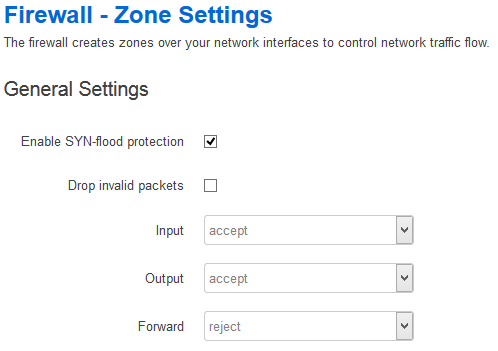
This is especially for your zone:

Get your network accessable:
Right now, you’re not able to connect to the new network nor are you able to do DNS requests if you use DHCP. This is because your zone’s INPUT rule is set to reject incoming traffic (to be more precise, these packets will hit the zone_Z_Wifi_Mitg_src_REJECT chain if you take a look in your iptables output).
Make an exception for DHCP in the tab “Traffic Rules” so that DHCP offers from 192.168.4.1 can reach your WLAN clients.
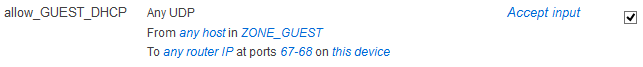
Do the same for DNS:

Tell your router about the new network:
Reaching this point you are able to initiate connections to clients of the LAN segment, but clients from LAN can’t connect to ZONE_GUEST, because there is no forwarding rule making this possible. Furthermore you can reach far away destinations like this website BUT: We did not enable NAT on LAN, so packets are routet to my website and unfortunately do not find their way back (router with IP 192.168.2.1 is asking it’s default gateway for a route to network 192.168.4.0/24 what will never be answered). Therefore, if you want to avoid double NAT (of course you want) you have to tell your router a route.
Network: 192.168.4.0
Subnetmask: 255.255.255.0
Gateway: 192.168.2.2 <– this is the LAN IP address of your AP, because it knows how to reach 192.168.4.0/24
Isolate clients within the WIFI_GUEST network:
To block traffic between clients in the network 192.168.4.0/24 you may take a look at the option “isolate” of the wireless configuration in OpenWRT. You can try if isolation is successful through a pingtest between two clients of this network before and after you isolated the clients with this option. If you don’t set this option you may think of other possibilities to protect your network against DNS poisoning, DHCP injections and so on.
Restrict access to certain services:
To restrict the clients in your network to use only allowed services it is the best option to set some firewall rules in the tab “Custom Rules” where you can add terminal commands that will be executed on firewall start. Here is an example (don’t change the command order unless you really know what you do):
# Insert (-I) entries into your public zone's forwarding rule ## Reject all traffic iptables -I forwarding_ZONE_GUEST_rule -j REJECT ## Reject all TCP traffic with reset flag to avoid unnessecary timeouts iptables -I forwarding_ZONE_GUEST_rule -p tcp -j REJECT --reject-with tcp-reset # Allow certain traffic iptables -I forwarding_ZONE_GUEST_rule -p tcp -m tcp --dport 80 -j ACCEPT -m comment --comment "Allow traffic on port 80" iptables -I forwarding_ZONE_GUEST_rule -p tcp -m tcp --dport 443 -j ACCEPT -m comment --comment "Allow traffic on port 443" # Reject traffic with destination LAN iptables -I forwarding_Z_Wifi_Mitg_rule -d 192.168.2.0/24 -j REJECT # Add a closing NewLine, otherwise the last command may be not interpreted correctly (e.g. because you did not use vi as editor).
What does it mean? First, a rule to reject all traffic that shall be forwarded from ZONE_GUEST to another is created. The chain forwarding_ZONE_GUEST_rule is a user chain. Don’t use system chains like zone_ZONE_GUEST_forward for your hacks. It works pretty fine if you restart the firewall when the AP is running. But these system chains are rebuild each time the corresponding interface is re-upped. That is also the case while booting -> firewall settings are applied, interfaces come up, rebuild, your hack is forgotten. Additionally every TCP packet is rejected with reset flag to avoid timeouts. Then rules are applied that allow traffic going to specific destination ports and finally access to LAN resources is prohibited.
Be careful with the interpretation of what these firewall rules are able to. Right now all traffic on TCP ports 80 and 443 is routet to the LAN and via gateway to the internet. Ok so far. But that does not mean that only HTTP(S) traffic is allowed. It means every connection with these ports, whether they are used for HTTP(S) as they were designed for or to transport other protocols is allowed. To ensure only HTTP(S) traffic is allowed you need to set up an OSI level 4 firewall (~proxy) like squid instead.
I work in a secondary school in Hungary and your blog has been a great help to me so far. I had followed your advice on how to set up radius on a raspberry pi, and now the system works and the teachers are happy :-).
This week, I am trying to separate students’ accounts from teachers’ accounts, so students wouldn’t be able to reach the local network. I followed your guide (http://steven-england.info/2014/11/01/openwrt-how-to-create-a-public-network-without-using-the-wan-interface/ ), but unfortunately it doesn’t work for me. Of course there are a few differences between our local network and your example, but I changed the relevant infos (eg.: our subnet mask is 255.255.0.0). My questions are:
– We have many openwrt based access points (mostly brand new TP-LINK WA901NDs), using fix IP addresses from 10.0.0.101 to 10.0.0.116 and disabled DHCP server as there is a standalone router for that purpose. The guest network interfaces would use almost the same IPs: from 10.0.1.101 and so on. My first question is: do I have to enable DHCP for the guest network as I can see in the screenshot on your site?
– I named both the firewall and the network interface the same name (ThanDiak), can it be a problem? (I replaced your names with mine everywhere, eg.: at the “Custom Rules” page.)
– Interestingly, my newly created interface doesn’t have a MAC address. Should I give it any? The same as the real one, or should I come up with something?
– Am I right that if I want to use radius as an authentication method later on, that I need to forward 1812 and 1813 ports as well?
The most important question of all:
– There is a section in your guide: “Tell your router about the new network”. I don’t know how to do that. 🙁 Can you tell me which panel to use?
Your help is greatly appriciated!!!
Hi Márton,
first of all thank you for your nice words. I will do my best to help you. But please be tolerant, this tutorial was made some time ago and right now I have no option to check the device I worked on 😉
– We have many openwrt based access points… -> if you built up your network like mine, DHCP offers of your central instance (the router) won’t reach the isolated clients in the guest network. In my case the router offers DHCP for the network .2.0/24 but not for .4.0/24. If you need DHCP in your guest network, turn it on (guest interface) and don’t forget to set the firewall rule for DHCP (UDP port 67-68) to allow DHCP offers from .4.1 to your clients.
– I named both the firewall and the network… -> I don’t know 🙁
– Interestingly, my newly created interface… -> huh… I don’t know how OpenWRT handles this internally. Unfortunately I’m not able to check it on the device I used. Next time I have access to it, I will check this.
– Am I right that if I want to use radius… -> no need to forward these ports. They are used “outside“ your guest network between AP and RADIUS server. The EAP communication between Client and AP is based on OSI L2. Just install wpad instead of wpad-mini and configure your interface to use WPA2 Enterprise.
– There is a section in your guide… -> that depends on your router. I don’t mean the AP. I am talking about the router that has to know a static route to your guest network. Otherwise if for example client 4.10 initiates TCP traffic to the internet, .4.1 forwards to .2.1 forwards to its standard gateway, response packets from the internet arrive at .2.1 but won’t be passed to the network .4.0/24.
Because of the not that easy to understand internals of OpenWRT I also had to try a lot with firewall rules and so on. Observing packet losses with iptables -L (which chain dropped my packets???) and observing tcp/udp communication with Wireshark (DNS request went out but became no answer, …) was the way I had to go…
If you need further exchange you can respond to my email I will send to you and we will write down the final answer in this blog post later on.
Hi Steven,
It’s an old post but you are still absolutely right in the fact that there’s not that many tutorials for that specific network setup! Yours is the only one I’ve found for far using OpenWRT.
Unfortunately, I was not able to make it work correctly. Are you aware of anything that is related to a specific OpenWRT version or a specific router model that could prevent that? Are you still using such a setup and if so, have you made any fine tuning on it?
I triple checked everything, only my IP numbering is different to integrate it into my current network.
Concerning the Guest interface not having a MAC address, I get the same thing and, according to your screen caps, you have the same thing too. Even if I use the ‘Override MAC address’ field and enter a valid MAC Address, the disply remains at 00:00:… So I don’t know what to think about that.
I even reseted the router to its default setting and started from scratch with the same result. The Guest wifi network will give me an IP address in the correct range but nothing goes beyond that. When I configure another wifi interface directly connected to the LAN, everything works and I have LAN and Internet access from that network.
Thanks for any help.
JF.
Hi Jeff, unfortunatly I’m not using this configuration anymore 🙁 But what exactly is your problem using this tutorial?
Hi,
you probably don’t use this config anymore, but for everyone who are trying to make this work and it doesn’t, make sure you have set the IPv4 gateway and custom DNS servers in the LAN interface to your main router IP (like it is shown in the first picture), because I didn’t and I spent hours on trying to get it work.
Hi, finished with tutorial but now in luci -> wireless overview the two wifi shows: “Wireless is disabled or not associated” and none of them starts.
Through putty, if i enter: iw list
it shows: interface combinations are not supported
any way to resolve this?
Thanks, good tutorial
Thank you! I knew this was possible but was struggling to get it working. Your guide was very useful.
I got a little stuck on the step “Tell your router about the new network,” so the following might be useful to someone:
In my setup both the AP and the router are using OpenWRT. in LuCI on my router, I had to go to “Network > Static Routes” and then input the values use listed to enable internet access to the guest network.
Hi Mr. steven, I have TP-LINK WR941ND v5.1 and its WAN is dead, How can I make broadband PPPoE connection by using one of four LAN ports instead of dead WAN, THANX.
Sorry I would like to tell you that my router ( TP-LINK WR941ND v5.1 and its WAN is dead ) has OpenWrt 15.05 firmware
Hi Steven,
thank you so much for sharing your config.
It help a lot and improve my knowledge with network and openwrt.
And thanks to Reid for the static route….
By
I have never written a static rule before, so I had difficulty understanding Reid. In case I am not alone, this is how it works:
Interface: lan (or whatever interface that points to your OpenWRT AP at static address 192.168.2.2)
Host IP: 192.168.4.0
IPv4 Netmask: 255.255.255.0
IPv4-Gateway: 192.168.2.2
Metric: empty
MTU: empty
Route type: unicast
And of course, it has to be set on the router and not on the AP.
I ran into trouble with the guest not getting on the internet. I could logon to the router, but that’s it. I found this page
blog.doenselmann.com/gaeste-wlan-auf-openwrt-access-point/
It is in German, but the 4 links to screenshots explain what to do to get access to the internet and block the local network from the guest network.
picture blog.doenselmann.com/wp-content/uploads/2015/09/guest_wlan11.png
picture blog.doenselmann.com/wp-content/uploads/2015/09/guest_wlan12.png
picture blog.doenselmann.com/wp-content/uploads/2015/09/guest_wlan13.png
picture blog.doenselmann.com/wp-content/uploads/2015/09/guest_wlan14.png
I hope I could somebody help
Hi! Thanks for your old tutorial… That was Brad new to me:D
I was just a bit confused about the static route setup.
I have a router (from my ISP…) And I have a openwrt device with a dumb AP and a guest wifi in there.
I setup your configuration in my openwrt device…
The static route is on the openwrt device. Right?
And about the setup? It says… Lan/guest target subnet gateway mtu …
What should i configure?
Thanks in advance
Hi there!
I have some trouble to reach the LAN from Guest (or to reach almost anything from guest).
I have my phone connected to the guest wifi ( IP, DNS etc are set as expected from DHCP ).
Ping from my phone to 192.168.4.1 works (I used same address as in the howto).
Ping from my phone to 192.168.1.252 works: it’s the IP address on my openwrt device on the LAN side.
But I cannot reach anything else.
Ping to 192.168.1.254 (gateway) not work, as well as ping to PCs on the LAN : 192.168.1.xxx
Is there anything I shall check ?